memetic authentication & identification
patent-pending • passwordless • multi-factor • multi-lateral • episodic
no text • no biometrics • no hardware
easy for users • hard for hackers
Visit: http://memeticidentity.com
accelerators • assessments • modelers • templates • DEMO
patent-pending • passwordless • multi-factor • multi-lateral • episodic
no text • no biometrics • no hardware
easy for users • hard for hackers
Visit: http://memeticidentity.com
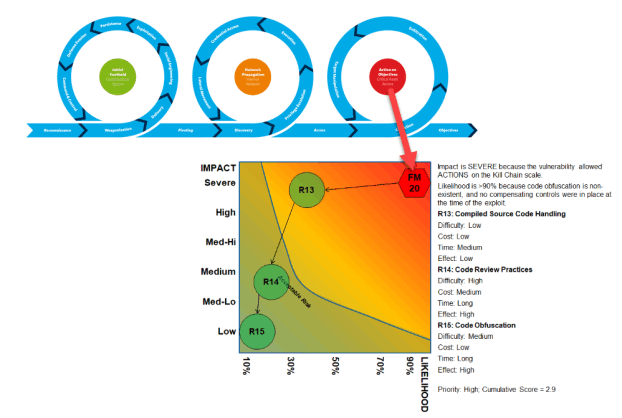
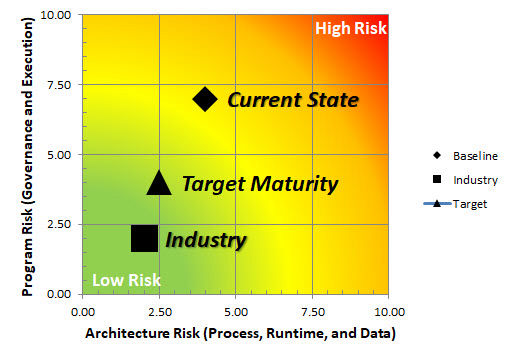
Our Breach Readiness Accelerator combines failure mode analysis, unified kill chain analysis, risk analysis, and business impact analysis to help you proactively plan for cybersecurity breaches by aligning and prioritizing technology improvements in a risk-informed manner. Our method can also be used retrospectively to help you prioritize mitigation efforts upon discovery of Indicators of Compromise or an actual breach.
Our Compliance Readiness Accelerator helps you prepare for SOC II Type 2 audits by identifying control weaknesses and addressing them before the audit period in a risk-informed manner, reducing the severity and number of findings during an audit. This tool is not limited to SOC audits, and may be readily adapted to other audit-control frameworks.
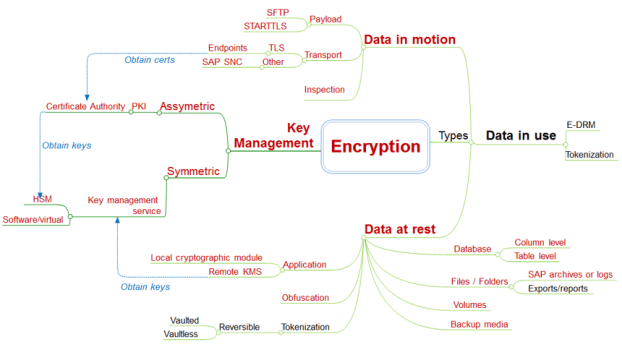
Our Data Protection Accelerator helps you rapidly improve your organization’s ability to defend against unauthorized disclosures and other forms of data loss, including customizable decision trees for determining where to apply which data protection techniques and solutions.
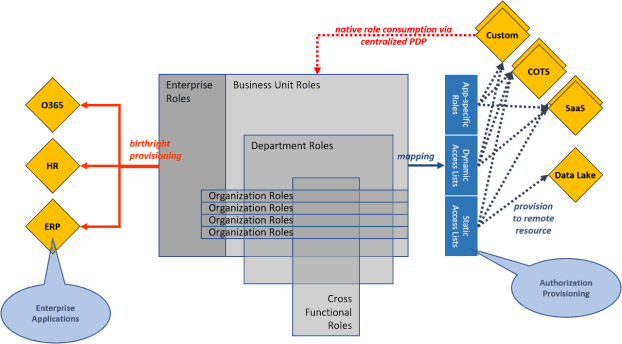
Our Fine-Grained Access Accelerator helps you determine the appropriate policy framework for fine-grained authorization (GBAC, RBAC, ABAC, PBAC). Our method accelerates policy modeling and helps you standardize run-time access controls across all of your apps to consistently enforce information barriers.
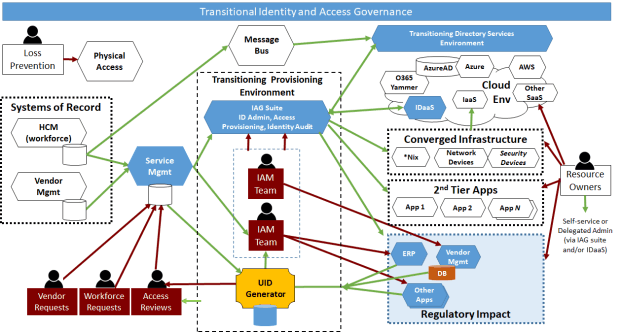
Our Identity Modernization Accelerator provides a migration template and project guidance method to help you transition from legacy identity management solutions to zero-trust cloud-based platforms where identity is the perimeter. It incorporates Just-in-Time (JIT) Privileged Access Management to improve the integrity of cloud and hybrid environments.
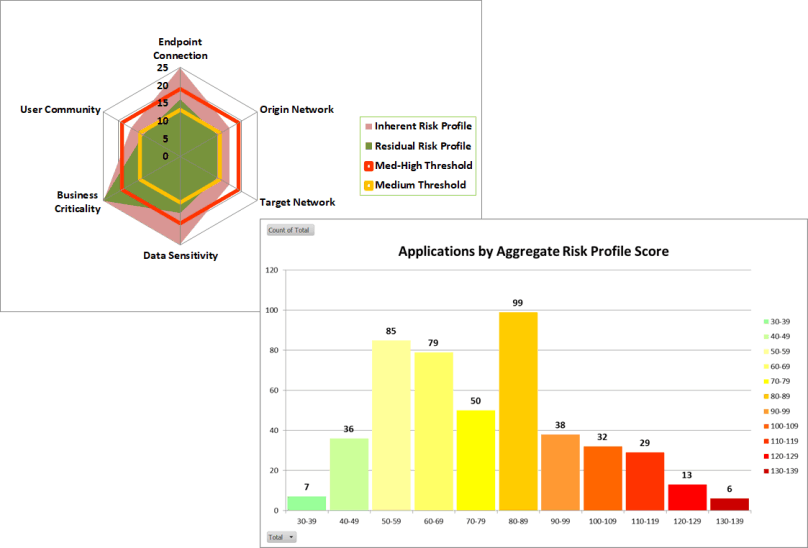
Our 3rd-Party Risk Assessment enables you to quickly and consistently identify, quantify, assess, and treat cyber risks resulting from your customers, suppliers, partners, and vendors. Our tool helps normalize risk quantification and incorporates results into your overall risk management program. It also automatically builds a risk distribution curve of your 3rd Party portfolio to help your prioritize risk mitigation efforts.
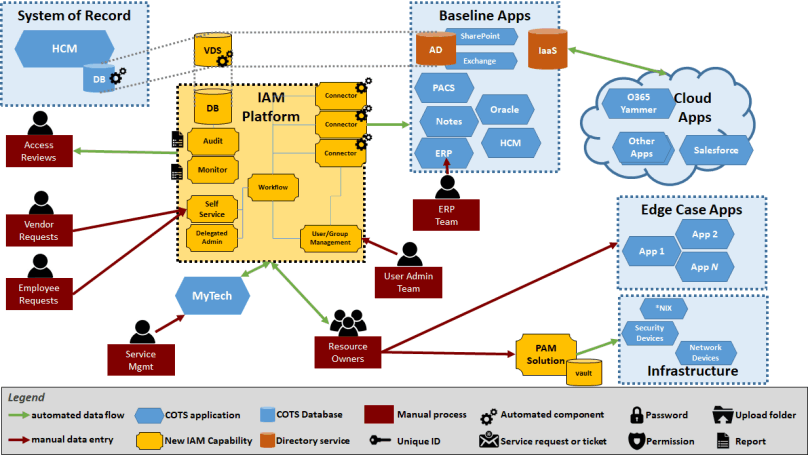
Our Authentication & Directory TuneUp helps you clean up directory schema and data, optimize performance, modernize your overall directory services architecture, and improve the login and authorization experience for your end users.
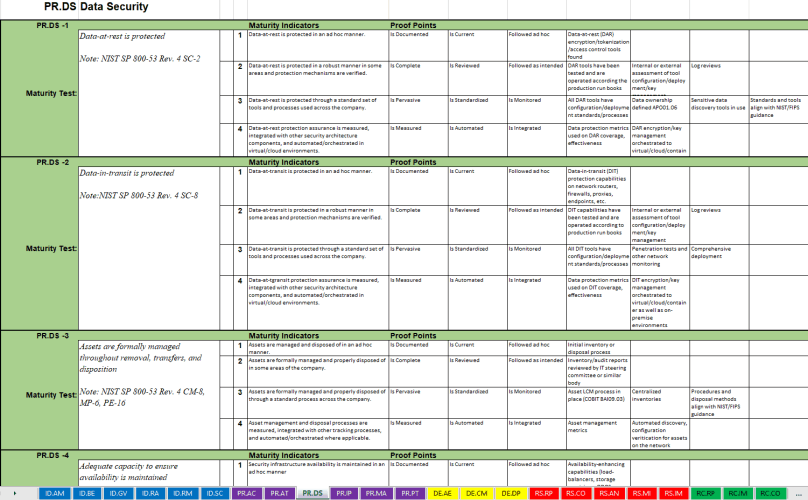
Our CSF Self Assessment enhances the NIST Cybersecurity Framework materials with our unique set of maturity tests, maturity indicators, and pre-defined proof-points. These testing criteria are pre-defined for each and every function, category, and sub-category defined in the framework. This tool helps you quickly document your company’s cybersecurity posture after establishing a baseline assessment so you can continuously improve and communicate your risk posture.
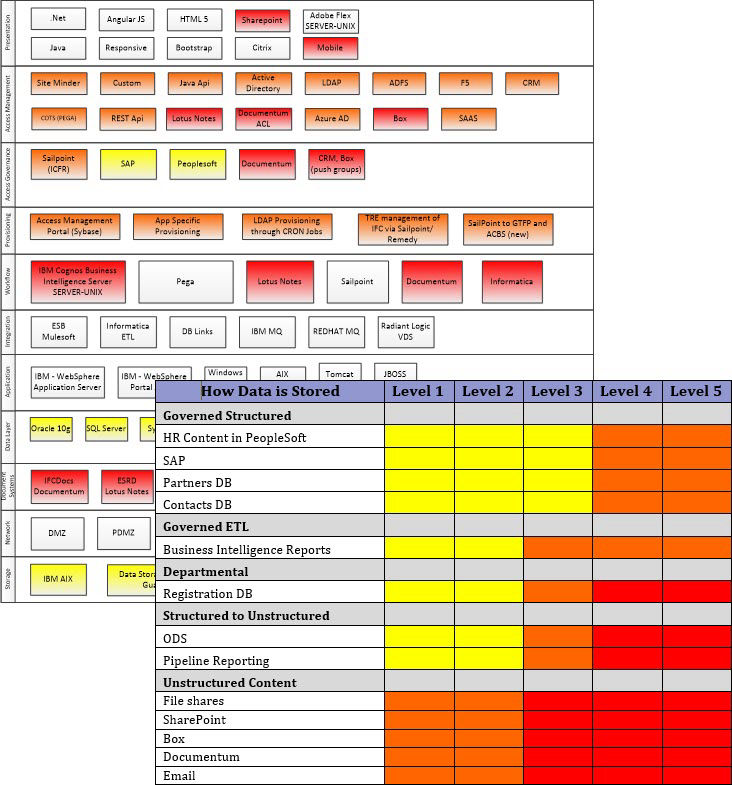
Our Privacy Risk Assessment helps you understand the technology implications of your company’s privacy obligations under CCPA and GDPR by visually identifying privacy "hot spots" and recommending strategies and tactics to reduce privacy-related technology risk.
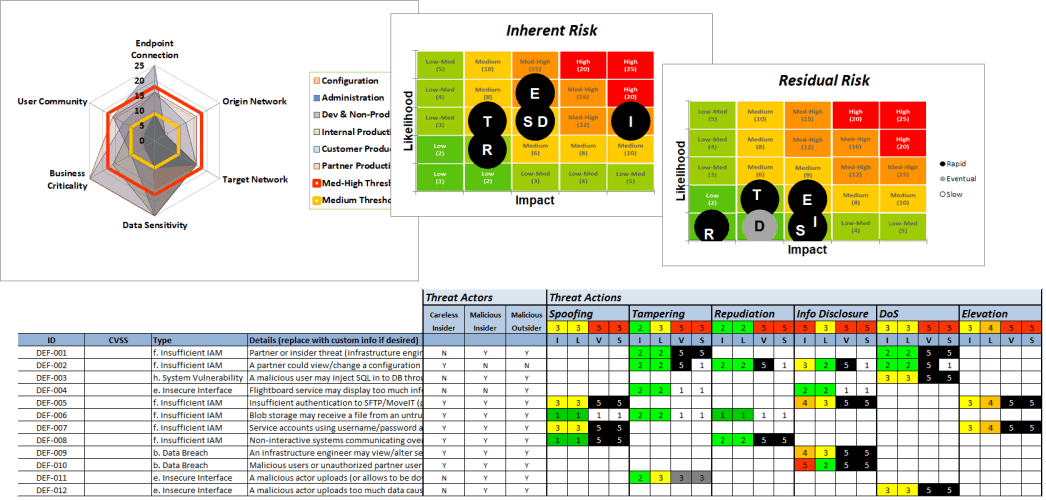
Our Agile Threat-Risk Modeler allows your development teams to quickly and consistently create detailed threat models and cyber risk assessments with minimal impact to your DevOps cadence.
This modeler is based on the industry-standard STRIDE model (spoofing, tampering, repudiation, info disclosure, denial of service, elevation of privileged). It comes preloaded with the top ten types of cloud-based threat vectors derived from the Cloud Security Alliance, as well as a basic threat actor library.
It allows practitioners to calculate the risk reduction of various controls that may be applied, including a business impact analysis component that helps your team prioritize which controls should be applied. It can even be tailored with controls defined from your control library.
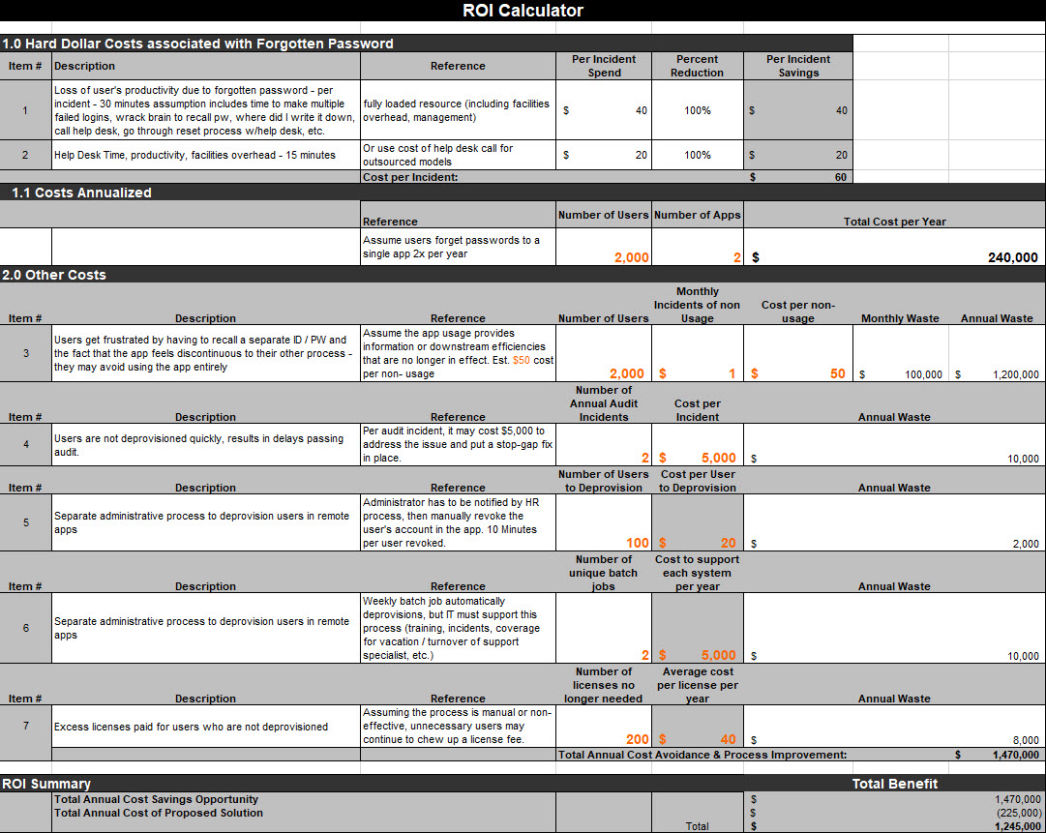
Our Business Case Modeler helps you develop solid risk-informed business impact analyses to cost justify and prioritize spending on cybersecurity, identity, privacy, and risk management projects.

Our KRI-KPI Library includes a prebuilt library of common cybersecurity Key Performance Indicators and Key Risk Indicators, along with tutorials and guidance on our method for deriving KRIs and KPIs specific to your organization.
Our Remote Working Security Primer is an instructor-led curriculum that can augment your current security awareness program for educating and training your workforce to be more secure when working from home (WFH).
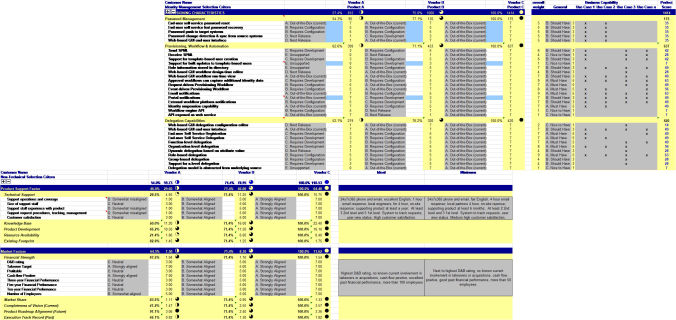
Our RFx Evaluation Matrices are customizable tools that facilitate objective collaboration between your technology and procurement teams when evaluating and selecting technology service providers.