
Developers aren't security experts

Security experts aren't developers

Is Agile an excuse to avoid documenting requirements?

Security teams aren't geared for Agile and often become bottlenecks or impediments to progress

All the static testing, dynamic testing, vulnerability scans, and pen tests in the world won't fix fundamentally insecure designs.
Create consistent data flow diagrams based on the six most common usage patterns, or develop your own custom flow diagrams
For each pattern, develop a multi-dimensional risk profile to aid in assessing risk

Using our prebuilt but extensible library of threat types, threat actors, and threat actions, quickly develop detailed threat-risk analysis

Enable technical and business teams to collaborate on identifying appropriate, actionable control plans based on risk reduction and business impact
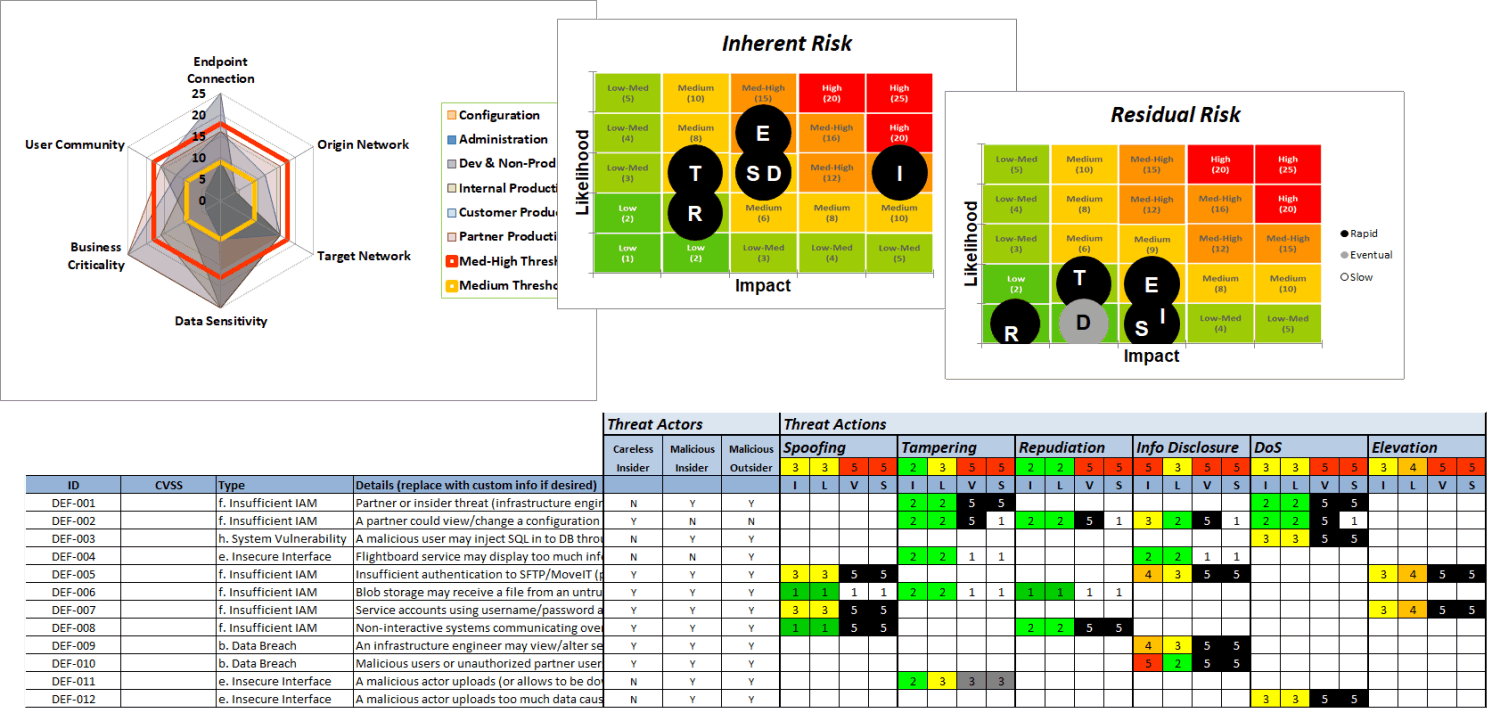
Our threat modeler starts by developing a multi-dimensional risk profile based on the six most common data flow patterns. For each pattern, the tool allows risk assessors to identify and analyze the threat types, threat actors, and threat actions. For each identified threat vector, the risk assessor can then apply organization-specific control plans to measure the risk reduction value of technical controls designed to mitigate the threats. The tool automatically generates inherent vs. residual risk heat maps to help visualize control plan effectiveness.

“Essentials” gleaned from high performing cybersecurity programs

Content crafted by cybersecurity experts and professional educators

Accepted practices compiled from hundreds of engagements

Agility delivered in compressed time and at reduced expense

Initial investment credited toward future enhancements
You select solution
We prepare agreements
NDA & SOW
Licensing & Support
You execute agreements
We send survey
You complete survey
We send toolkit
We arrange support
We schedule key events
We complete tailoring
We mentor your squads
You Deliver Success!